As organizations accelerate toward AI assisted development, the limits of traditional static application security testing are becoming increasingly clear. Deterministic, rule-based SAST tools were designed for slower release cycles, human-written code, and centralized CI pipelines. In modern environments where AI generates large volumes of code and teams ship continuously, those assumptions no longer hold.
To address these gaps, a new category of tools has emerged under the broad label of AI SAST. These tools aim to improve detection accuracy and scope such as logic flaws and cross-file vulnerabilities, reduce noise, and keep pace with modern development velocity. However, not all AI SAST tools are the same.
AI SAST vs AI-Powered SAST Tools
Many tools marketed as “AI SAST” are more accurately described as AI-powered SAST. In these systems, AI is applied after traditional static analysis has already run. The core detection engine remains rule driven, while AI is used to assist with tasks such as:
- Generating remediation suggestions or hot fixes
- Triage and severity adjustment
- Flagging likely false positives
While this approach can improve usability, it does not fundamentally change what the tool can detect. These tools still inherit the blind spots of traditional SAST, particularly when it comes to complex application logic and novel frameworks.
True AI SAST goes further; instead of operating only on the output of deterministic rules, AI is part of the detection process itself. These systems reason about how code behaves, how data flows through an application, and what a piece of code is intended to do. As a result, AI SAST can:
- Detect complex logic flaws and authorization issues
- Understand context that traditional pattern matching misses
- Adapt to new frameworks and coding styles more quickly
- Identify vulnerabilities that span multiple files or functions
This distinction is critical when evaluating the top SAST tools. AI-powered enhancements can reduce friction, but only true AI SAST can expand coverage and keep pace with the realities of AI-led development.
This guide highlights some of the top AI SAST and AI-powered SAST tools, expanded and modernized for today’s engineering and AppSec teams. Our aim with this guide is to provide a summary of our opinions driven by customer and third-party research to show where each tool excels, where it falls short, and how well it fits modern development environments.
1. Arnica: The AI SAST Leader for Developer-Native, Agentic Application Security
Arnica is the agentic AppSec platform designed specifically for AI-driven software development. It powers both traditional static analysis and next-generation AI SAST through the multi agent engine, Arnie.

While most tools only scan pull requests or rely on CI integration, Arnica analyzes every push, every branch, and the entire backlog in real-time and continuously. This ensures full codebase coverage from the start without requiring pipeline configuration.
Arnie’s AI SAST combines deterministic static analysis with multi agent reasoning. This allows Arnica to:
- Detect more complex vulnerabilities, like logic flaws and access control issues
- Offer secure fix suggestions instantly
- Eventually understand code context across entire repos
This hybrid approach enables both repeatability and intelligence. Developers don't need to configure anything. The rules follow them across repositories and branches. Arnica scans code on push, on pull request creation, nightly, and across all feature branches. This eliminates blind spots typically caused by pipeline only scanners or IDE plugins that developers rarely adopt.
Arnica also offers one-click secret mitigation that removes secrets from commits and the entire git history. It also supports automated remediation paths for code vulnerabilities, reducing noise and backlog.
Because Arnica communicates findings through Slack, Teams, Jira, and in pull requests, developers don't need to adopt new tools. Most issues are resolved before PR creation and AppSec teams see significantly reduced review volume. Arnica then prioritizes risks based on severity, exploitability, and business impact. Competing tools typically prioritize only by severity, which causes alert fatigue.
Arnica is ideal for:
- Organizations using AI code generation
- Teams struggling with noisy, slow, or inaccurate scanners
- Enterprises needing full code coverage without pipeline friction
- Dev teams wanting fast, actionable feedback
- Organizations with legacy languages or frameworks with low traditional SAST support
- AppSec teams seeking automation and high-impact prioritization
Arnica is built for the agentic era where AI writes a growing percentage of code and security must keep pace.
2. Corgea
Corgea is an AI SAST tool that uses large language models to analyze code with more contextual awareness than traditional rule-based scanners. It focuses on reasoning about application behavior rather than relying solely on predefined patterns.
Where it works:
- Identifying some logic level and framework specific issues
- Catching vulnerabilities that are difficult to express as static rules
- Reducing dependence on large, manually maintained rule sets
Where it doesn’t:
- AI SAST only, no out-of-the-box hybrid SAST solution, which is less deterministic where it matters
- Mapping findings to real ownership and workflows
- Automated remediation or large-scale backlog management
- Replacing a full application security platform; they offer SAST only
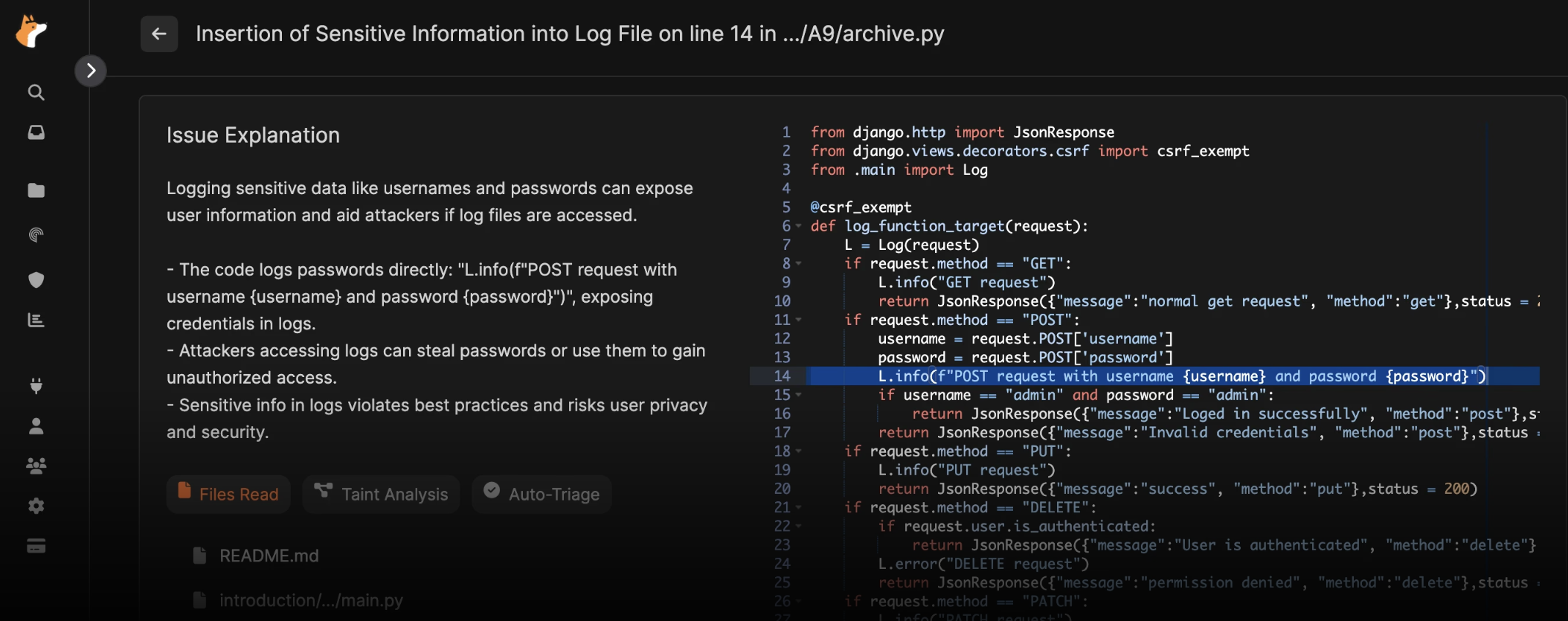
3. ZeroPath
ZeroPath is a modern alternative to traditional rule-based SAST, using LLMs combined with elements of static analysis to interpret how an application operates. Instead of relying on large rule libraries, ZeroPath attempts to analyze control flow, data flow, and general application behavior. This gives it a different feel than pattern-driven scanners, but it also creates new gaps, especially in practical prioritization and business relevance.
Where it works:
- Can identify some issues related to application logic
- Supports natural language prompts for custom checks
- Generates patches for certain findings
- Reduces some types of rule-based false positives
Where it doesn’t:
- Full scans on large repositories can be slow
- Limited real understanding of organizational context such as which assets matter, which code paths are actually used, or who owns a fix
- Generates patches, but does not align with developer-native workflows
- Reliance on traditional CI/CD pipelines makes visibility harder and remediation slower
4. Semgrep
Semgrep is a fast, rule-driven static analysis tool focused on customization and developer control with new AI SAST capabilities. It uses a pattern matching approach that avoids the complexity of abstract syntax trees, and it has recently introduced AI features to assist with rule creation and triage.
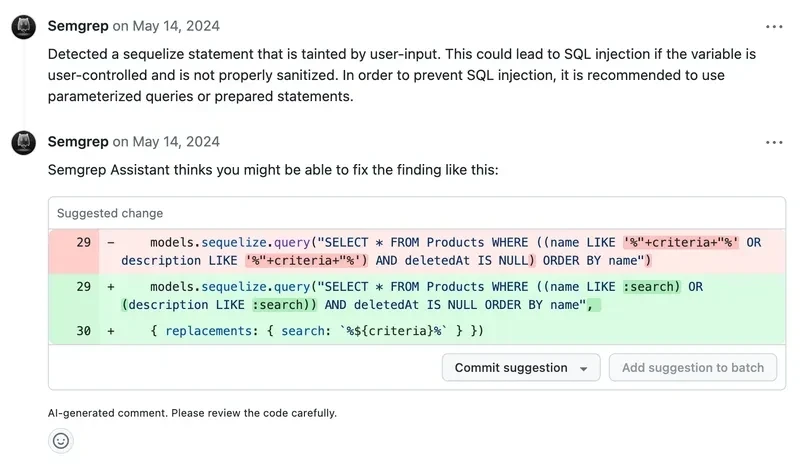
Where it works:
- Fast scans, suitable for running on pull requests
- Custom rules can be written quickly with straightforward syntax
- Active community providing a large catalog of shared rules
Where it doesn’t:
- Can require extensive manual engineering and ongoing security engineering investment to maintain and scale rules effectively
- Built-in, deterministic rules can be noisy and often miss issues that require deeper context
- Pricing changes have made usage difficult for many teams, leading to the creation of Opengrep, an open source fork of Semgrep, supported by Arnica in collaboration with several other vendors in theAppSec space
5. Snyk Code
Snyk began as an SCA-focused product and later expanded into SAST, now with AI-powered SAST capabilities. Its developer-friendly branding emphasizes quick setup and IDE integrations that surface issues as developers type. This approach is convenient for lightweight checks, but it also exposes limitations in depth, accuracy, adoption, and scalability.
Where it works:
- Provides immediate feedback inside popular IDEs such as VS Code and JetBrains
- Offers AI generated suggestions that help fix basic or well-understood issues
- Supports common web development languages including JavaScript, Python, Java, and Go
Where it doesn’t:
- Lower opt-in and adoption due to pesky IDE alerts and false positive noise
- Minimal ability to create meaningful custom rules or advanced security logic
- Pricing escalates quickly as the engineering organization grows
- Can misidentify safe code as risky because it lacks contextual understanding
6. Veracode
Veracode provides cloud-hosted static analysis and AI-powered SAST. It’s typically adopted by organizations that prioritize governance and compliance requirements. The platform is built primarily for centralized security teams, not developers, and its workflows reflect this orientation.
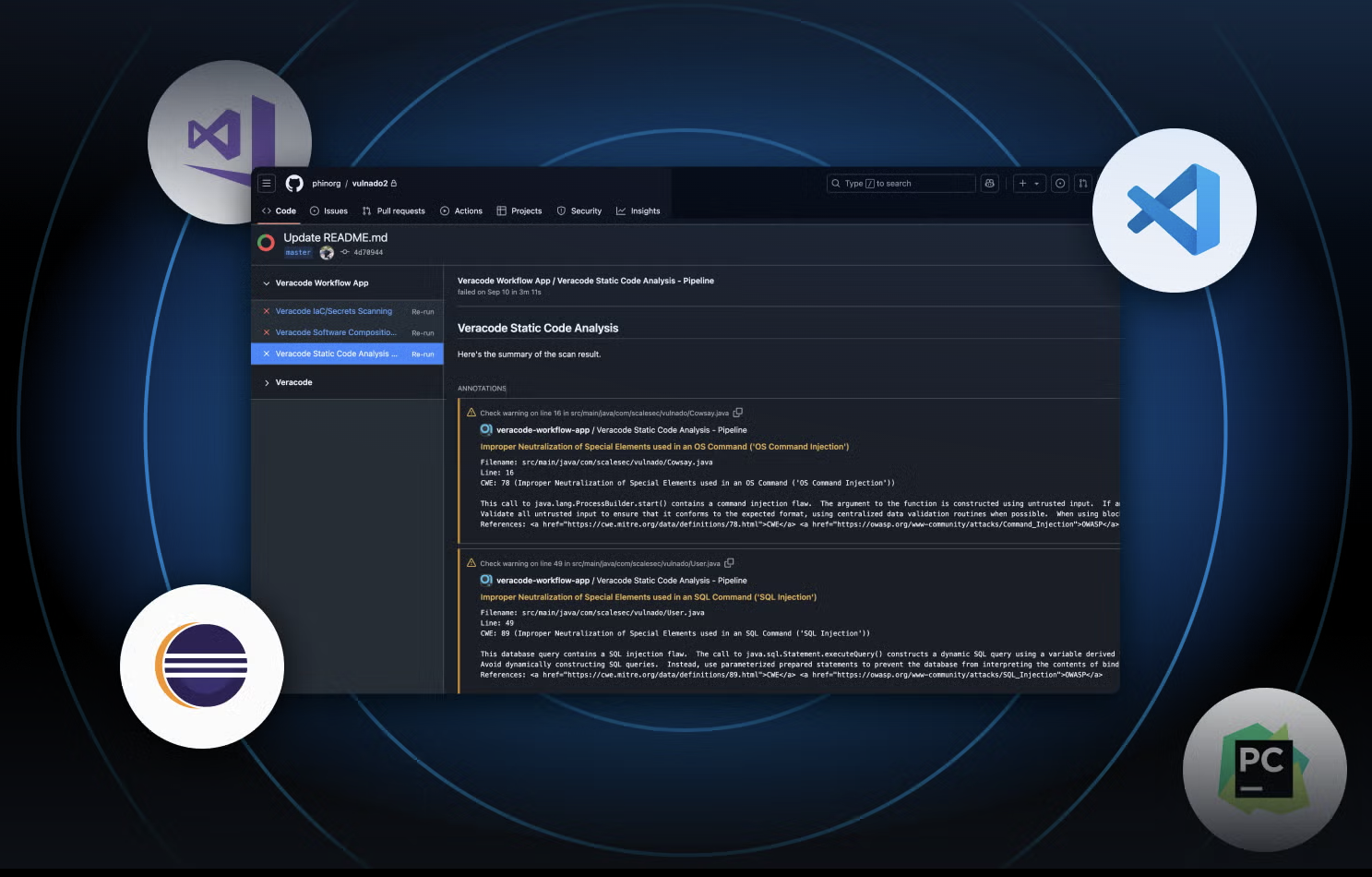
Where it works:
- Handles large enterprise applications with wide language coverage
- Offers AI assisted remediation suggestions intended to speed up triage
- Fits organizations that enforce security gates through a central AppSec function
Where it doesn’t:
- Steep learning curve and not-as-friendly developer workflows
- Full scans are noticeably slower compared to modern cloud native scanners
- Manual reviews and false positives are reported by customers
AI SAST Tools are Now Mandatory, Not Optional
AI SAST has become essential as AI generated code accelerates development and expands the attack surface, forcing security teams to adopt tools that can prevent vulnerabilities during code generation, automatically detect complex risks, reduce noise, fit naturally into developer workflows, scan continuously across branches and backlogs, and provide real remediation rather than simple detection.
While most tools in the market deliver only incremental improvements, Arnica is unique in securing the entire lifecycle from generation to push to pull request to backlog through its combination of hybrid AI SAST, agentic rule enforcement, pipelineless scanning, and automated remediation.
Reduce Risk and Accelerate Velocity
Integrate Arnica ChatOps with your development workflow to eliminate risks before they ever reach production.




