The SANDWORM_MODE Campaign Is Live - Here's How Arnica Customers Can Respond in Real Time
A new software supply chain worm is actively spreading across the npm ecosystem. Tracked as SANDWORM_MODE, this campaign has already compromised at least 19 malicious packages across two npm publisher aliases, targeting everything from popular Node.js utilities to AI coding tools like Claude Code and OpenClaw.
The attack is sophisticated. On import, compromised packages harvest developer and CI secrets, exfiltrate data via the GitHub API with DNS tunneling as a fallback, poison GitHub Actions workflows, and persist through git hooks that survive into future repositories. Packages are typosquatted against high-traffic developer tools - casting a wide net across the install patterns most likely to produce accidental hits.
The Real Problem: "Are We Exposed?"
When campaigns like SANDWORM_MODE break, every security team faces the same scramble. Leadership asks a simple question: “Are we affected?” In most organizations, that question takes days, sometimes weeks, to answer.
Why? Enterprise-wide visibility into software dependencies is still one of the biggest unsolved challenges in application security. Organizations run hundreds or thousands of repositories, each pulling in a web of open source packages. Most teams don't maintain a continuously updated Software Bill of Materials across their entire footprint. Those that do often rely on snapshots that are stale before they're complete.
So when a zero day campaign drops, security teams are stuck manually triaging repositories, chasing down engineering leads, and hoping they haven't missed something buried three layers deep in a transitive dependency tree.
The gap between "a threat exists" and "we know our exposure" is where real risk lives.
Today's Release: Filter Your SBOM by Zero Day Campaign
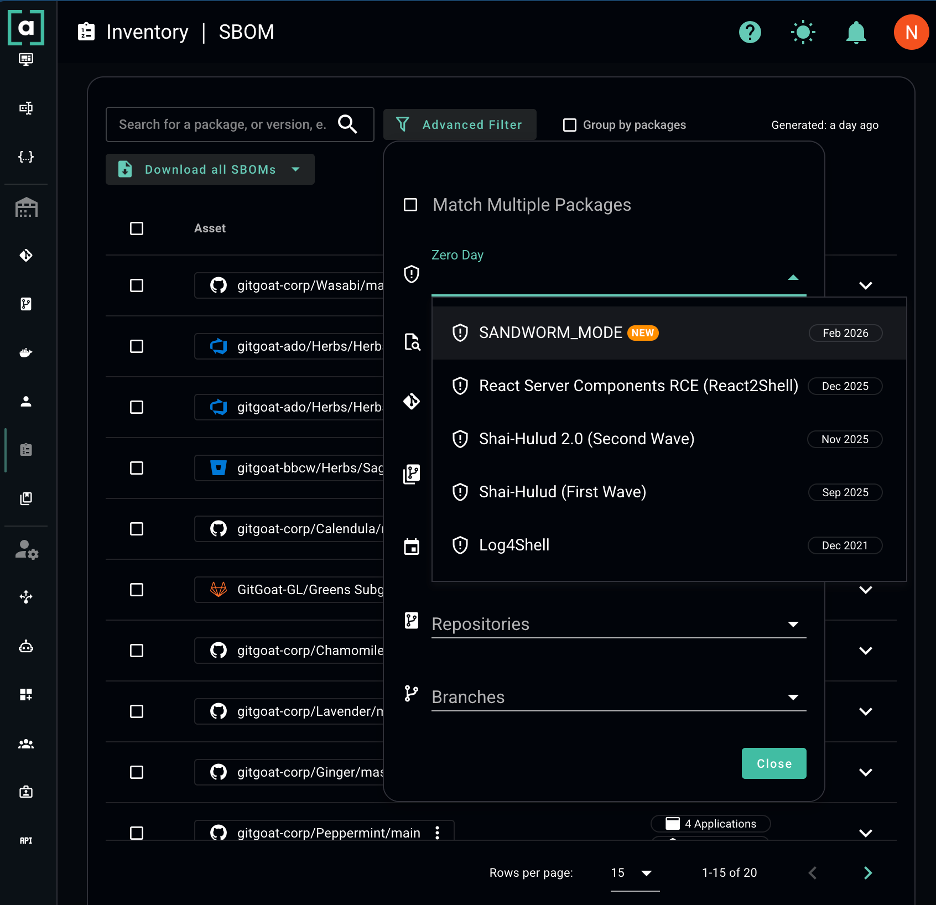
Today we're releasing a new feature that closes that gap. Arnica customerscan now filter their enterprise-wide SBOM based on active software supply chain zero day campaigns. Customers can start filtering immediately with SANDWORM_MODE.
Arnica's SBOM now includes a dedicated Zero Day campaign filter in Advanced Filters. When an active supply chain attack is identified, Arnica maps the known indicators of compromise against your organization's continuously maintained, enterprise-wide SBOM, including malicious package names and affected versions. Now you have access to an enterprise-wide filtered view showing exactly which repositories and applications are potentially impacted with in seconds. All without manual triage, spreadsheet wrangling, or waiting for someone to "check their stuff."
Built for Speed
We designed this feature to that when a zero day campaign breaks, response time isn't a nice-to-have, it's the entire game.
Arnica maintains a living, enterprise-wide SBOM that updates continuously as developers commit code and dependencies change. When we identify a new supply chain threat campaign, we push the campaign filter to all customers sothey can query their exposure instantly in real-time, not after a scan or an audit.
With SANDWORM_MODE, our team identified the campaign and made the filter available to customers the same day. That's the standard we hold ourselves to. To check your exposure:
1. Navigate to your Arnica SBOM page under Inventory
2. Open Advanced Filters
3. Select Zero Day and choose the SANDWORM_MODE campaign
That's it. You'll immediately see every repository in your organization that may be affected.
What Makes SANDWORM_MODE Dangerous
This isn't a run-of-the-mill typosquatting campaign. SANDWORM_MODE builds on the Shai-Hulud worm lineage that first tore through npm in September 2025, compromising over 180 packages in under 24 hours. This latest iteration adds several alarming capabilities
- MCP server injection: the malware targets AI coding assistants (Claude Code, Cursor, Copilot) by deploying malicious Model Context Protocol servers with embedded prompt injection
- GitHub API exfiltration with DNS fallback: stolen secrets leave through multiple channels, making detection harder
- Git hook persistence: a global init.template Dir setting ensures malicious hooks survive into every new repository on the infected machine
- CI workflow poisoning: injected pull_request_target workflows serialize and exfiltrate secrets from your pipelines
- LLM API key harvesting: a clear signal that attackers are following developer adoption patterns into AI toolchains
The breadth of targets spans crypto tooling, developer utilities, and AI coding tools and suggests an operator casting the widest possible net across the modern development stack.
Available to All Arnica Customers
This capability is available today across all Arnica tiers, from Free through Enterprise. We believe every organization deserves to know their exposure when a supply chain attack is active, regardless of plan level.
If you're an existing customer, the SANDWORM_MODE campaign filter is already available in your SBOM view. If you're not yet using Arnica, there's never been a more urgent time to get enterprise-wide visibility into your software supply chain.
Software supply chain attacks aren't slowing down they're getting faster, more sophisticated, and harder to detect. The organizations that weather these storms are the ones that have already invested in continuous visibility. An up-to-date, enterprise-wide SBOM isn't a compliance checkbox. It's the foundation that lets you answer "are we affected?" in minutes instead of days.
Get started with Arnica and see your software supply chain exposure in minutes, not days.
Reduce Risk and Accelerate Velocity
Integrate Arnica ChatOps with your development workflow to eliminate risks before they ever reach production.



